Archive for category Programming
Traffic Simulation
Posted by Jurgen in Data Visualisation, Programming, Simulation on December 1st, 2014
 Some time ago I implemented a traffic simulation program in JavaScript, a little less advances than this one (non Java) but with full source disclosure. To make it part of eDesign.nl this is the post associated with it. Check it out for a one crossing simulation or a double crossing simulation using the same engine.
Some time ago I implemented a traffic simulation program in JavaScript, a little less advances than this one (non Java) but with full source disclosure. To make it part of eDesign.nl this is the post associated with it. Check it out for a one crossing simulation or a double crossing simulation using the same engine.
Virtual Switchboard
Posted by Jurgen in Programming, Simulation on November 27th, 2014
 Back when I was in highschool, during some physics lessons we worked with ‘systeemborden‘ (Dutch for ‘system boards‘ or ’switchboards’). It was to learn basic logic gates. They were boards with component on them which you could wire, to make a system. For instance, you could connect a button to a led, which made that when you pressed the button, the led would turn on. You could also instead connect the button to an AND-component, along with a sound-sensor (microphone) and connect the output of the AND-port to the led. That way the led would show light when a sound is made and the button is pushed. There are a lot of other and more complex combinations possible with a lot more different components too. I thought to virtualize it in HTML5 and JavaScript. Have look and play with the switchboard I made (the source code is free and not obfuscated).
Back when I was in highschool, during some physics lessons we worked with ‘systeemborden‘ (Dutch for ‘system boards‘ or ’switchboards’). It was to learn basic logic gates. They were boards with component on them which you could wire, to make a system. For instance, you could connect a button to a led, which made that when you pressed the button, the led would turn on. You could also instead connect the button to an AND-component, along with a sound-sensor (microphone) and connect the output of the AND-port to the led. That way the led would show light when a sound is made and the button is pushed. There are a lot of other and more complex combinations possible with a lot more different components too. I thought to virtualize it in HTML5 and JavaScript. Have look and play with the switchboard I made (the source code is free and not obfuscated).
Flags for PHP
Posted by Jurgen in Languages, Programming on October 22nd, 2013
 In my last post I wrote about the enumerated type (Enum) for PHP. In C# an Enum can have multiple values when it has the [Flags] attribute. A flags enum can be seen as a bitwise mask which can be used to combine boolean properties of an entity into one single integer property. This might come in handy when filtering on these properties. In this article I show my implementation for a flags enum in PHP and demonstrate the use of it in an example.
In my last post I wrote about the enumerated type (Enum) for PHP. In C# an Enum can have multiple values when it has the [Flags] attribute. A flags enum can be seen as a bitwise mask which can be used to combine boolean properties of an entity into one single integer property. This might come in handy when filtering on these properties. In this article I show my implementation for a flags enum in PHP and demonstrate the use of it in an example.
The enumerated type for PHP
Posted by Jurgen in Languages, Programming on June 9th, 2013
Whenever a procedure accepts a limited set of variables one could use an enumeration. Enumerations make for clearer and more readable code, particularly when meaningful names are used. A page at MSDN states the benefits of using an enumeration include:
- reduction of errors caused by transposing or mistyping numbers,
- simplify changing values in the future,
- code is easier to read, which means it is less likely that errors will creep into it and/or
- ensuring forward compatibility. With enumerations, your code is less likely to fail if in the future someone changes the values corresponding to the member names.
Enumerations are a must if your software solution spans across multiple projects and/or if the team you work is rather large. Read the rest of this entry »
Avoid becoming a spam source
Posted by Jurgen in Programming, Security, Spam protection on August 21st, 2010
 The number one rule in programming is not to trust external data, especially not user data. One of the reasons not to trust user data is the threat of hackers searching for injection possibilities. When you start develloping web applications you’ll soon learn the dangers of SQL injection. This might be the most important form of injection, but by far it is not the only one out there: cross site scripting is another good example. If your application sends out mail, you might want to make sure you sanitize user input as well as the application could be a magnet for spammers who’ll send spam mail using your IP. Read the rest of this entry »
The number one rule in programming is not to trust external data, especially not user data. One of the reasons not to trust user data is the threat of hackers searching for injection possibilities. When you start develloping web applications you’ll soon learn the dangers of SQL injection. This might be the most important form of injection, but by far it is not the only one out there: cross site scripting is another good example. If your application sends out mail, you might want to make sure you sanitize user input as well as the application could be a magnet for spammers who’ll send spam mail using your IP. Read the rest of this entry »
The Game of Office Decoration
Posted by Jurgen in Programming, Simulation on April 22nd, 2010
 This week I had a discussion with a colleague of mine about decoration for the new office rooms we hired. We thought of an Arduino based project, because it would just be cool to have some fun with the gadget.
This week I had a discussion with a colleague of mine about decoration for the new office rooms we hired. We thought of an Arduino based project, because it would just be cool to have some fun with the gadget.
We could make a giant board filled with buttons with a led in them. You’d press a button to toggle it. This board could be controlled by an Arduino and display several things on it. A clock for instance or news headlines from an arbitrary RSS feed or… since they’re buttons, Conway’s Game of Life! Read the rest of this entry »
Math behind a world sunlight map
Posted by Jurgen in Algorithms, Image processing, Simulation on May 14th, 2009
 My neighbour has a map of the world on the wall. You can see it from the street in front of his house. It has a backlight but that only illuminates half of the map. The transition from day to night is shaped like a sine wave most of the time. It actually is a physical world sunlight map. Of course, you can simulate this with a computer too. There even is an instance using Google maps.
My neighbour has a map of the world on the wall. You can see it from the street in front of his house. It has a backlight but that only illuminates half of the map. The transition from day to night is shaped like a sine wave most of the time. It actually is a physical world sunlight map. Of course, you can simulate this with a computer too. There even is an instance using Google maps.
As many roads lead to Rome multiple ways are possible to this simulation. One could model the sun, earth, maybe more and start ray tracing. This approach would include solar eclipses but is quite heavy by means of the load on the processor. Because of the number of calculations involved in ray tracing is quite high. The way I choose to describe fully in this article is one close to it. Using vectors pointing from a sphere (earth) to a point (sun) I map a Mercator projected map of the world on the sphere. The challenges included are the yearly orbit of earth around the sun and it’s 23.5° tilted 24 hour spin. Read the rest of this entry »
Textual difference detector
Posted by Jurgen in Algorithms, Text processing on May 7th, 2009
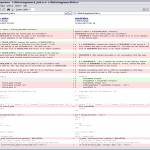 Today I uploaded my textual difference detector to the eDesign examples. This is an example application demonstrating the theory of applying the Levenshtein algorithm to detect differences between two versions of the same text. Also, the ‘Find the differences‘ post is updated with a link to this example.
Today I uploaded my textual difference detector to the eDesign examples. This is an example application demonstrating the theory of applying the Levenshtein algorithm to detect differences between two versions of the same text. Also, the ‘Find the differences‘ post is updated with a link to this example.
This example takes two texts as input and outputs one merged text marked with what was deleted and what was added. Take a look and feel free to download the source code. This also inlcludes the Levenshtein algorithm source code.
Challenge Hash
Posted by Jurgen in Algorithms, Security on May 5th, 2009
 The Internet is a crowd and everybody in it can potentially hear what you say. Methods have been developed to prevent this and ensure identity, integrity and authenticity. Often these three can be seen as properties of encryption. Encryption implies the possibility of decryption. Passwords are precious things you don’t want others to decrypt and read. With a technique called challenge hashing you don’t need to have any worries about it. Challenge hashing is a technique used to verify a password on site B which was sent from site A without sending the password in plain text. This article covers how. Read the rest of this entry »
The Internet is a crowd and everybody in it can potentially hear what you say. Methods have been developed to prevent this and ensure identity, integrity and authenticity. Often these three can be seen as properties of encryption. Encryption implies the possibility of decryption. Passwords are precious things you don’t want others to decrypt and read. With a technique called challenge hashing you don’t need to have any worries about it. Challenge hashing is a technique used to verify a password on site B which was sent from site A without sending the password in plain text. This article covers how. Read the rest of this entry »
Sudoku Logic – part I
Posted by Jurgen in Algorithms on May 1st, 2009
 If you haven’t heard of Sudoku puzzles (数独, sūdoku) you’ve either been sleeping under a rock or been space traveling for quite a while. These 9×9 square puzzles originating from around 1900 became an international hit in 2005. Sudokus appear in newspapers, online and special sudoku puzzle books all-over-the-world. And as if that is not yet enough Sudoku TV shows and all kinds of variants of the puzzle are made. One can solve a sudoku using logic only. Because of this computational algorithms to solve every possible Sudoku must exist. This is part one in the series on such algorithms. Read the rest of this entry »
If you haven’t heard of Sudoku puzzles (数独, sūdoku) you’ve either been sleeping under a rock or been space traveling for quite a while. These 9×9 square puzzles originating from around 1900 became an international hit in 2005. Sudokus appear in newspapers, online and special sudoku puzzle books all-over-the-world. And as if that is not yet enough Sudoku TV shows and all kinds of variants of the puzzle are made. One can solve a sudoku using logic only. Because of this computational algorithms to solve every possible Sudoku must exist. This is part one in the series on such algorithms. Read the rest of this entry »
